To open the Dark Mailer is need to double click on the icon called "dm" on the desktop. Below is the icon should look in the Desktop folder or in the folder where you have installed the DarkMailer
After opening the program main window will appear the same,as follows:
In this window, the first thing we have to do is simply touch the LOAD button located above the left to load the text file that contains advertising. Below is the main window, with the button highlighted to be opened for identification purposes.
Once that window is opened, another search window will appear, so to put the path where the file is ad text.It is recommended to save the HTML file in the same folder where is installed DarkMailer, in this case "Desktop" in
Windows.
Below is a figure which is clearly the type of window that is to appear.
This will locate the file you need.
Where it says "Search" appears as the default desktop, then you must select the path to find the correct file.
Once the display shows the correct file, double-click it and automatically be charged, being as follows.
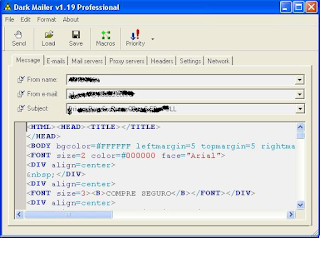
The image shown above is as it should be. The message is loaded in sight "HTML Code" does not mean that customers receive the message that way, you will receive properly.
In the "From Name", "From Email" and "Subject" should not change anything, it automatically for this product have been charged with 20 different names, 20 different Emails and between 5 and 10 different Subjects. The program is set to every 30 mails that are sent to change the sender, email and the subject, making them rotate all contained in each shipment, to prevent servers sending spam detected.
Now, we load the email lists.
For that, we must go to the tab that is next to the one we are looking at right now is "message" ... the next tab is "emails" here we see how to load the txt list containing all emails from potential clients
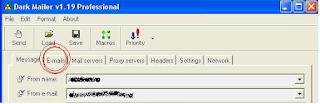
The image we're seeing just shows the top of the window. In this, there are the tabs to configure all the shipping. In that image is highlighted with red circles show the tab "emails" which we clicking to visualize.
Once done, you should see the following window:
Well, I will explain a bit what we see in this window.
In this rectangle that appears empty and is labeled "this list is empty" there will appear all the lists to be loaded for shipping.
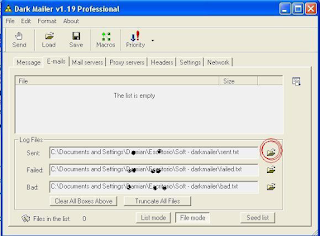
Then we have 3 lines down under the title of "Log Files" here means that configure what we want the program saved in the logs.
We can configure to save a file of emails sent, failed and non-existent.
We will configure the logs to start. NOTE: only be configured once, no need to configure these logs every time you close and open the program.
The first thing to touch is the yellow icon that appears on the right side of the window, as is shown below:
Once you touch this button opens a window style that was opened when Load the HTML file. In this window just what you need to do is locate the folder where we have the DarkMailer (desktop will be the default folder), once
found, the open and automatically displays all the files inside. Without touching nothing but enter into any other
folder, touch the button and ready OPEN (see figure below)
Once this process appear the path to this file on the line provided. To place the other two logs (Failed and Bad) is necessary to do the same procedure with this.
Ready, once finished loading the logs, we will proceed to load the files containing the mails, called by us "email list", which contain 30 000 addresses each.
To download these files, we must go on the rectangle that is labeled "this list is empty" and click the right mouse button. This will display a list with three options, of which we select "Add", as shown in the picture below.
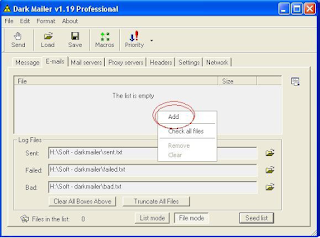
Pressing this option will open a search window classic, we request you give the path to the files you wish to add to our "mailing list." This window is similar to that found when loading the HTML file and Log files seen before.
It is very important that all txt files sent to them in the file "Softw - DarkMailer.Zip" Be original unzipped folder within the program, to avoid confusion. That is if the program folder on the desktop, and this folder is called "DarkMailer" then we must create within the folder "DarkMailer" a subfolder called "lists", and unzip these files there. The folder "lists" would be replaced the following to the famous "Data" folder of AMS used in previous shipments. In short, it should be thus Desktop / DarkMailer / Lists Then in the search dialog of the wizard will guide txt files to this folder, to show us all the files we have available.
Note: While all files included, you should charge for a six lists, to avoid confusion and to better control the flow of emails. After showing us all, make the first double-click to load. When you repeat the process over five times more to be loaded for 6 to start the shipping lists, being as follows.
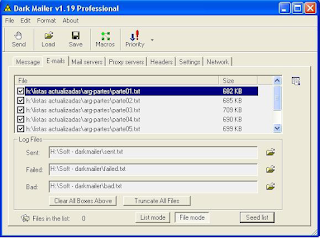
Keep in mind that in the left side of each list in each row, there is a check box that appears primed each time you add a list. If this box is uncheck, and we have not yet processed a shipment, we checked, otherwise the program will not let us continue.
In summary, for here we have loaded the text to send, we will automatically set the fields "From Name", "From Email" and "Subject", we have also posted the names and path to save the logs of each shipment and finally we loaded six lists we send.
Once done, the rest of the flaps should not be playing, because the mail server, the proxies and settings, will be changed from the central machine and send them to a file, that should only be replaced at no must now change any option in that case you may not leave the shipping correctly, so I recommend "Do not touch anything that is not specified in the manual"
Before starting with the shipping, they will apply for performing only time a configuration change. This change is going to do as I said for the only time recently, and will allow us to automatically detect the DNS of the connection you are using and also configure an option that will allow us to pause shipments if the connection is dropped or disconnected, and take them up again if the same program achieved after several attempts to reconnect. For this, they must be facing the computer and ask assistance, MSN or by PHONE.
Now if we are in a position to begin shipments. As these items are sent by remote servers and Proxies may note several flaws, the most likely first start and has 2000 deliveries and 0 errors, numbers and then change to normal, remaining at approximately 80% of incorrect shipments.
If you stay here until the all clear, then we will touch the send button as shown in the figure below. (The button is in the top left of the window progrm).
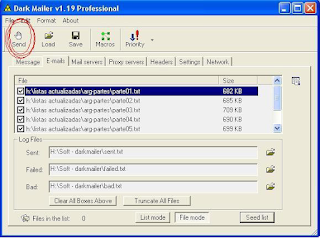
Pressing this button will start sending emails, starting with the first list marked the end, come to the second and so on until end all.
Once complete, touch the OK button and repeat the charging process of emails, deleting first those already harged and sent. To do so, touch the right mouse button and select "Clear List", after that, the list is rejected, and the rectangle with the words "this list is empty" as before. Redo all the steps of loading lists and sending emails.
Below is a picture of how emails are processed with this program.






















